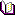Difference between DbDefence's and SQL Server's Masking
DbDefence's and SQL Server's security differ in their approach: SQL Server assumes that DBA always has permissions for everything, DbDefence assumes that DBA can be evil.
The table below compares major masking features.
| SQL Server Masking | DbDefence | |
| Bypassing Masking | Yes | No |
| Different masks for different logins | No | Yes |
| Protection from DBA | No | Yes |
| Unmasked values are visible in database files and backups | Yes* | No |
| Can hide column completely | No | Yes |
| Can prevent database copying | No | Yes |
| Can mask computed column | No | Yes |
| Can mask FILESTREAM column | No | Yes |
| Can mask TEXT,NTEXT column | No | Yes |
| Masking methods | Only 4 functions | Wide range of T-SQL functions |
| Supported versions | SQL Server 2016 and above | SQL Server 2008 R2 and above |
Bypassing Masking
Consider an attacker that has sufficient privileges to run ad-hoc queries on the database and tries to 'guess' the underlying data. Let's assume that we have a mask '*' defined on the [Orders].[Creditcard] column, an attacker, connects directly to the database and starts guessing values:
SELECT NAME, CREDITCARD from Orders WHERE CREDITCARD LIKE '4849%'
Result with SQL Server Masking:
| NAME | CREDITCARD |
| Jon Doe | * |
| Kim Son | * |
| Donna Rosa | * |
SQL Server matches unmasked data with WHERE clause and displays rows. By narrowing WHERE in the SELECT statement, an attacker can reveal the actual data protected by SQL Server masking.
DbDefence isn't affected.
Result with DbDefence Masking:
0 rows returned.
An attacker can't guess values with DbDefence's Masking.
Different masks for different logins
SQL Server offers only one mask for a column. With DbDefence you can completely mask or hide a column for a particular login, partially mask for another and leave it visible for those who are allowed.
Protection from DBA
With SQL Server's Masking, a privileged attacker may use EXECUTE AS to run SELECT statement on behalf of an authorized user:
EXECUTE AS USER = 'AllowedUser'; SELECT * FROM Orders;
With DbDefence's Masking, this statement will still show masks. It is possible to enforce security further and see the actual data only if a user is logged with the specific password. It prevents data leak if a DBA overrides the password.
Unmasked values are not visible in database files and backups
SQL Server's Masking isn't designed to protect data-at-rest. An attacker can see all data in clear text unless transparent data encryption (TDE) is applied. Until SQL Server 2019, TDE was included in the expensive Enterprise Edition. With SQL Server 2019, TDE is available in the Standard Edition.
DbDefence implements masking for all SQL Server editions and always combines it with complete data-at-rest encryption. Unmasked values are never seen in backups or raw database files.
Hidden column
DbDefence can hide columns instead of showing a mask. Displaying masked data can give to an attacker the direction for the attack.
Masked types
DbDefence can mask FILESTREAM or computed column types. Accordingly to the documentation SQL Server can't mask FILESTREAM or computed columns.
Masking functions
Accordingly to the documentation SQL Server offers only 4 functions to be used with masking. DbDefence offers a wide range of functions available in T-SQL.
Supported SQL Server versions
DbDefence implements masking for all SQL Server editions (64-bit), including Express and LocalDB.