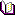Data Masking rules
New Feature: Different masks for different logins.
Data masking functionality is available only in "Only Encryption, Maximum Transparency" mode.

Masking rule structure:
[FOR: LOGINNAME]
<TABLE NAME>
<FIELD NAME>
! || <MASK VALUE>
<TABLE NAME>
<FIELD NAME>
! || <MASK VALUE>
...
! as a mask value hides the column.
See Multiuser masking for FOR:.
The number of rules is not limited. Strings starting with '--' are considered as comments and ignored.

The picture above shows masks for three fields. The first rule is for the field called LAST_NAME in the table called TABLE_NAME. Instead of displaying actual value, DbDefence will display string '***' The second rule masks the field called FIELD_NAME_INT in the table name TABLE_NAME. Mask is an integer, 0 instead of a real value. The last rule shows a mask with SQL function RIGHT used to display two last chars of the column.
Important: The type of the masks must match the type of an underlying column.
Usually, an application expects a value of a specific type defined. When a mask has a different type, the application may quit unexpectedly, crash or work unpredictably. For example, if you mask the field called TOTAL, which is an integer, and mask is a string '***', then the application will be confused and crash.
Who will see real values?
The real values will be shown to: