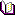dbd_add_module
exec master..dbd_add_module @path sysname
The procedure adds and loads PKCS#11 module to SQL Server. Initially specified module is verified for consistency, PKCS specifications. The module should be a DLL with exports accordingly to PKCS#11 specification. Additionally Dbdefence verifies digital signature for the module. Modules with missing digital signatures or with improper PKCS#11 format are declined. Modules from unauthorized vendors are declined. Currently Dbdefence supports modules from the following vendors:
- Activecrypt Software
- SafeNet
If you would like to add support for particular vendor or your own digital signature please contact support@activecrypt.com
After validation the path is saved in the registry under HKEY_LOCAL_MACHINE\SOFTWARE\ActivecryptSoftware\DbDefence\pkcs11_modules\x64 for 64-bit SQL Server and HKEY_LOCAL_MACHINE\SOFTWARE\ActivecryptSoftware\DbDefence\pkcs11_modules\x86 for 32-bit SQL Server. Important: This registry path is used by both SQL Server and encrypting tool.
Platform compatibility
If you deploy DbDefence as a part of your solution or use it's API you may encrypt the database with 32-bit or 64-bit version of the API. SQL Server's platform may differ from the platform of encrypting tools. PKCS#11 module may be registered for x64 platform, but be missing for x86. As result, 32-bit Encryptor may load the module, but 64-bit SQL Server may not. In this case Encryptor will fail to encrypt the database because it verifies the module and the key on SQL Server prior to encryption operations. This helps to avoid cases when database is encrypted with the key or the module unavailable for SQL Server process. In such case the database would be unaccessible.